Analysis of Enron e-mails reveals structure of corrupt networks
CAMBRIDGE, Mass. — Political thrillers that portray a “web of corruption” get it all wrong, at least according to an analysis of e-mails between Enron employees. The flow of the famously corrupt corporation’s electronic missives suggests that dirty dealings tend to transpire through a sparse, hub-and-spoke network rather than a highly connected web.
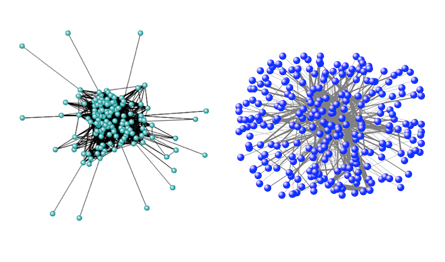
Employees who were engaged in both legitimate and shady projects at the company conveyed information much differently when their dealings were illicit, organizational theorist Brandy Aven of Carnegie Mellon University in Pittsburgh reported June 1 at an MIT workshop on social networks. The distinction is visible in the network of e-mails among employees, which takes the shape of a central hub and isolated spokes when content is corrupt, rather than a highly connected net of exchanges.
While today Enron is associated with corporate fraud, for years the energy and commodities company was a Wall Street darling. Fortune magazine named Enron America’s most innovative company for six consecutive years ending in 2000. But by the next year, the U.S. Securities and Exchange Commission was investigating the firm’s dealings.
“They were not only innovative technologically and administratively, but also in their accounting practices,” said Aven.
Aven’s analysis compared communications regarding three legitimate innovative projects and three corrupt ones that went by the names JEDI, Chewco and Talon. Communications regarding the shady deals took on a hub-and-spoke shape, a setup that maximizes secrecy and control. A small, relatively informed clique occupies the hub at the center, communicating with protruding spokes that don’t share ties with each other. The hub gets information from the spokes, which in their isolation are less likely to whistle-blow and can be played off each other.
Recognizing that content alters flow is crucial, said Ramakrishna Akella, an expert in information management from the University of California, Santa Cruz. Much of network modeling relies on statistics and algorithms that too often ignore content, he said. “Mining content is very insightful,” said Akella. The sudden appearance of new words or acronyms, for example, can signal the emergence of innovations.
That the sneaky behavior employed to cover the corrupt “innovations” at Enron might have been revealed just by diagramming who is e-mailing whom suggests that the structures of social networks might be a good diagnostic tool. Probing the shapes of social networks might help investigators identify electronic dens of intrigue, such as people communicating within a terrorist network, said Aven.
And the work suggests that networks aren’t just static conduits for information.
“It’s intriguing,” said Aven. “We’ve treated social networks as contained plumbing systems directing the flow of information, but we should think about them as water that carves river beds of social relations.”
Aven’s analysis revealed that, on average, employees sent roughly five e-mails about legitimate projects for every one about those that were corrupt. Transitivity — the tendency of two people who know the same person to also know each other — also dropped markedly in the network of corrupt communications. And reciprocity — back-and-forth rather than one-way communication — plummeted.
Read full story at Science News



Disinformation Campaign Proves Effective as Anti-SOPA Strike-Breaker
January 19, 2012 Leave a comment
Two or three days ago, announcements were broadcast on various Media Outlets stating that two bills in the Congress and the Senate, SOPA and PROTECT-IP were effectively “Dead-in-the-Water,” resulting in the cancellation (or extreme reduction) of what would have been an extremely disruptive– and therefore highly dramatic– strike/protest by Major Internet Companies against the proposed legislation.
The fact that no sources were actually named, as well as the coordinated nature of this spurious disinformation campaign, indicates that this legislation, involving a precipitous curtailment of the Civil Liberties in the United States, indicates a scope of political interests far beyond those of the Entertainment Industry.
History shows us that a curtailment of Civil Liberties is never instituted without an eye to a further attack on those same liberties at a later date.
This debate is not over. Expect to hear opponents to these bills caricatured as disgruntled pirates of popular entertainment, 20-somethings living in their mothers’ basements, who want to continue downloading music and movies without having to pay for the privilege.
Expect to read further, and ever more disturbing, developments in the coming months.
View A Legal Analysis of S. 968, the PROTECT IP Act [PDF] from the Congressional Research Service
Filed under activism, American, American political discourse, Blog, Blogroll, business, Civil Rights, class war, Commentary, culture, culture industry, Democracy, disinformation, Economic Democracy, economy, Events, Government, Human Rights, information, information dissemination, legal, life, media, news, Opinion, Political Hypocricy, politics, propaganda, Rights, social engineering, society, technology Tagged with business, class war, conspiracy, corporate malfeasance, Corporate Personhood, Corporate Welfare, corporations, disclosure, economy, flow of information, Government Secrecy, internet, news, politics, propaganda, PROTECT IP, Rupert Murdoch, SOPA, world order, Worthless Mass Media